Cryptocurrency continues to gain popularity with about 145 million adult Americans currently owning or previously owning cryptocurrency, even with an increasing number of investors being conned out of their digital assets because of their inexperience in investing and lack of understanding of the social laws governing the security and protection of their digital assets through hot and cold storage wallets. This makes new investors the primary targets for con artists. The cons are not slowing the trend down. According to a recent study, Americans who have never bought cryptocurrency before believe they are likely to do so for the first time next year as a result of the falling stock market and rising inflation.
For this report, Overwatch examined allegations and recent sightings of fraudulent and counterfeit hot and cold cryptocurrency wallets, focusing on the Ledger Wallet, which is acknowledged as one of the most well-liked hot and cold wallets available. Our analysis pinpointed several problems investors encounter when storing their cryptocurrency for protection.
Hot and Cold Storage and Their Scams
Investors in cryptocurrencies have two primary options for protecting their money: Hot and cold wallet storage. The easiest way to distinguish between the two is that a hot wallet is online and frequently connected through apps, but a cold wallet is offline and generally a handheld digital device. The other less popular option is to leave purchased digital currency on the exchanges.
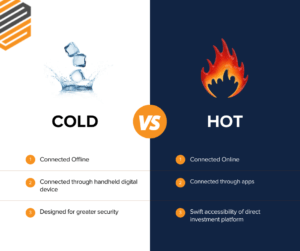
A hot wallet’s fast accessibility of investing directly from a smartphone or computer app draws investors in large numbers. The ease with which one can now invest in digital money increases the potential of fraud for thousands of people. However, the federal government has recently issued warnings about cybercriminals actively impersonating reputable cryptocurrency investing firms and convincing investors to download phony mobile apps to steal cryptocurrency. However, these criminals have a history of using high-quality counterfeit cold wallets with established backend access to compromise investors’ digital assets. This is typically done by providing a pre-seeded device or establishing malware on the device prior to shipment. Once an investor receives the device and attempts to transfer currency from an exchange or another wallet, the fraudsters will be able to obtain the funds. We mention this to demonstrate that there is no superior storage solution with the product’s absence of carefulness.
In a Private Industry Notification published by the FBI on July 18, 2022, titled “Cyber Criminals Create Fraudulent Cryptocurrency Investment Application to Defraud US Investor,” the FBI described how fraudulent hot storage wallets operate. According to the report, cybercriminals persuade victims to download a fake app to add cryptocurrencies to their wallets. The victims later seek to withdraw money from the app, but they are informed via email that they must first pay taxes on their investments. The victims are still unable to receive their cryptocurrency withdrawals even after paying the supposedlevy. This fraud is only one of numerous hot wallet scams involving cryptocurrencies that analysts have come across recently.
Recent Scams Reported
Ledger has provided a list of current phishing attacks and many alert messages starting in December 2020 on its website. Many alerts are regarding the prevalence of fake hot wallets on the market and the structure of cold wallet frauds that use Ledger as a front. Online investors have been continuously reporting being victims of scams over the past few weeks. Overwatch analysts have also noticed other suspicious activity related to using fake Ledger applications that can be found on app stores like the Microsoft Store and the Google Play Store.
For example:
- On June 12, 2022, a Reddit user reported a suspicious Ledger Live app was self-installed on their computer with a logo that did not match the mentioned company branding. Also found were misspelled words on the app’s landing page, where the user was requested to update their Ledger device.

- On July 17, 2022, an additional Twitter user captured a screenshot from the Microsoft App store, revealing that a fake hot wallet app was established on the platform posted under a legitimate cryptocurrency cold wallet company, resulting in the user losing $20k.

- On July 18, 2022, a user on Trustpilot reported that they purchased a counterfeit Ledger Wallet, which appeared tampered with before opening.
- On July 19, 2022, a Reddit user captured screenshots of a downloaded fraudulent Hot Storage app that provided fake Recovery seed phrases to steal any transferred currency.

These schemes are not being used as a novel way to defraud cryptocurrency investors. Cybercriminals still follow the same playbook: they lure unsuspecting investors into engaging fake Ledger Wallets, entice users to download apps or visit phishing websites, and then steal any currency entered.
Our Investigation
So what are the current market trends that investors should be aware of? Overwatch analysts investigated and found that Ledger Hello is one of them, and it’s available on the Microsoft Store. However, after a thorough search, only three reviews could be found, one of which was a user warning about the application claiming that it steals your money and wallet recovery seeds.

Following this discovery, analysts searched in preparation for further reports mentioning Ledger Hello. They found a Reddit user report stating their cryptocurrency was stolen from the same Ledger Hello app downloaded from the Microsoft storefront.

In addition to our investigation, analysts ran advanced searches for Ledger Nano X and Ledger Nano S devices. Analysts found four devices being marketed on Amazon from the United Arab Emirates. The tip was based on user reports that the investors had purchased counterfeit Ledger wallets on Amazon.

It appears that the item was bought from an Amazon seller who has since left the marketplace. Analysts were able to locate an archived version of the landing page that promoted the product, nevertheless.

To further our study, we looked for any hints that fake ledger wallets were being bought, sold, or obtained in dubious marketplaces on the dark web. Our investigation turned up a fake Chrome Device Manager browser add-on that claimed to be a Ledger Nano S extension and was obtained from the Google Play Store. Investors drawn to this extension would think it was a credible hot wallet storage solution due to the extension’s internet connection. However, confirmation through the official Ledger website showed that this browser extension is not affiliated with the company, and its users are not encouraged to use it.
 Our research into the dark web also turned up a forum where people talked about a set of Nano S ledgers bought in bulk on Alibaba. Following the adage “too good to be true,” investors interested in purchasing the item should view the product’s low pricing as a warning sign.
Our research into the dark web also turned up a forum where people talked about a set of Nano S ledgers bought in bulk on Alibaba. Following the adage “too good to be true,” investors interested in purchasing the item should view the product’s low pricing as a warning sign. 
These counterfeit gadgets are presented in premium packaging that aims to resemble the real thing closely. However, there is a good chance that the device has been tampered with or pre-seeded. This frequently occurs with Chinese online markets, not only for cryptocurrency hardware.


Our Assessment
According to the aforementioned study, seventy-four percent of cryptocurrency investors, or nearly 107 million Americans, bought for the first time in the last two years. However, according to the Federal Trade Commission, over 46,000 customers claim to have lost over $1 billion in cryptocurrency to scams since the beginning of 2021. This is partially due to cryptocurrency being in its infancy and the naivety of new investors, unsuspecting of the tactics of fraudsters.
Due to the significant expansion of the cryptocurrency sector, Overwatch predicts that in 2023 there will be a rise in the use of fraudulent apps. To target their victims for cryptocurrency scams, fraudsters will continue to take advantage of app marketplaces and create high-quality counterfeit digital wallets, concentrating on how eager new investors are to enter the digital investment arena. Should this occur, inexperienced investors unaware of the insider’s secrets risk losing tens of thousands of dollars more than we have seen in the past.
This analysis was carried out by analysts using advanced search terms on a variety of social media sites and dark web forums. In addition, we examined the marketplaces for cryptocurrency apps on app stores including the Microsoft Store, Google Play Store, and Apple App Store. Subsequently it becomes a game of “Whack-a-mole” because fraudsters continue to add and withdraw applications from these platforms. The same is true for online merchant sites like Amazon. With that said, it’s crucial for investors to be knowledgeable about the applications they use and to avoid getting cryptocurrency cold wallets from unlicensed vendors.
For investors interested in purchasing a Ledger Cold Wallet specifically, or utilizing the Ledger app, both products should only be acquired through the official Ledger.com website.